Risk-Based Vulnerability Management: What to Fix First (With a Simple Model)
Key Takeaways
- Most teams patch by severity score that’s the wrong starting point.
- Asset criticality and active exploitation status matter more than a CVSS number.
- A simple four-factor model can cut through backlog paralysis fast.
- If you’re not asking “is this being exploited right now?”, you’re missing the most important question.
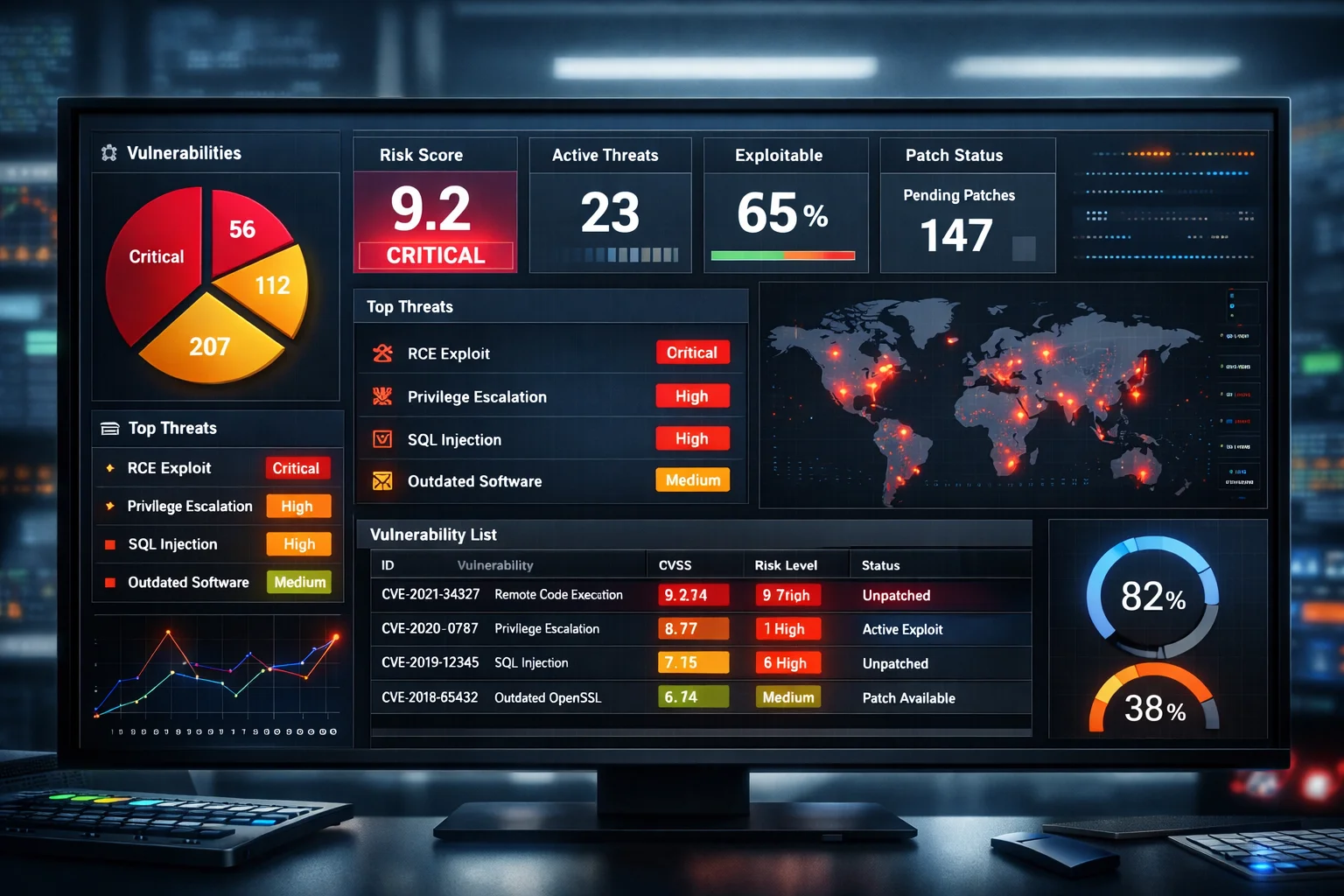
Your scanner just finished. You’ve got 4,000 findings, 312 marked “Critical,” and a ticket queue that makes your stomach hurt. So what do you fix first?
That’s the question most teams can’t actually answer. And it costs them.
The Backlog Problem Isn’t a Capacity Problem
Most security teams think the backlog is growing because they don’t have enough people to patch fast enough. That’s rarely the real issue.
The real issue is prioritization. When everything looks equally urgent, nothing gets done quickly. Teams spin trying to figure out what matters, approval chains slow down, and the queue keeps growing.
A 2023 study from CISA’s Known Exploited Vulnerabilities (KEV) catalog showed that only a small fraction of known vulnerabilities are actually exploited in the wild. Patching everything equally is like treating a paper cut the same way you’d treat a broken leg the math doesn’t work.
The backlog grows not because teams are slow. It grows because there’s no clear model for what “important” actually means.
Why CVSS Scores Are Only Half the Picture
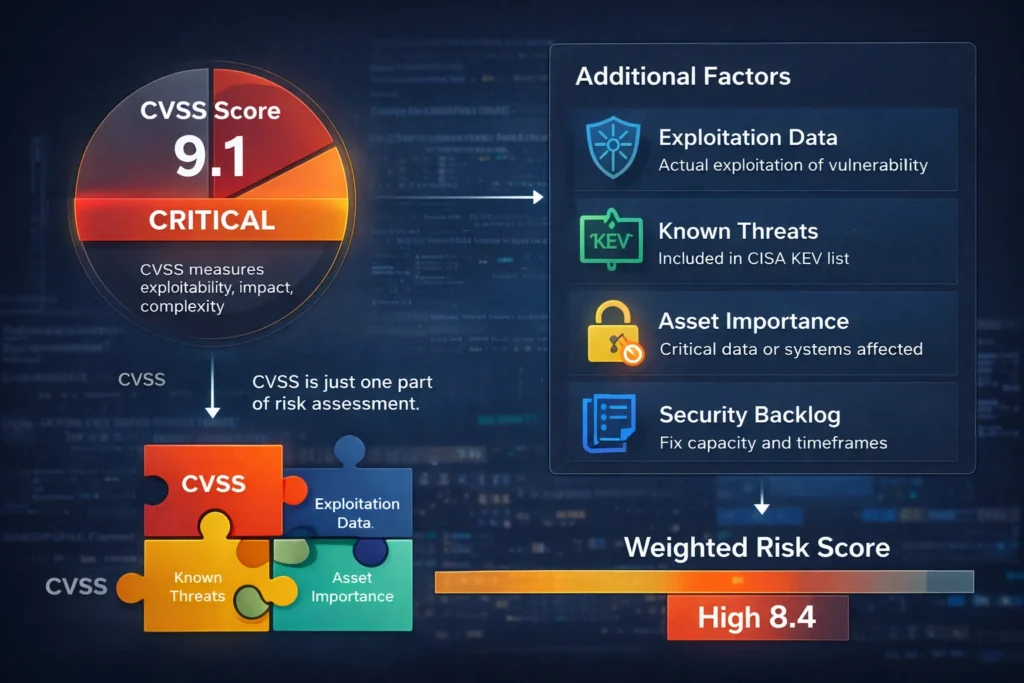
CVSS scores were built to measure severity in a vacuum. A score of 9.8 tells you the vulnerability is technically dangerous it doesn’t tell you whether anyone is actually using it to attack systems like yours.
Relying only on CVSS is one of the most common mistakes in vulnerability management lifecycle programs. You’ll end up patching a high-score vulnerability on a test server no one can reach while leaving a medium-score issue wide open on your customer-facing database.
Context is what CVSS doesn’t give you. Three things matter just as much as the score:
- Is it being exploited right now? Check CISA’s KEV list. If it’s on there, it jumps to the top of the line full stop.
- What asset does it live on? A CVSS 7 on a server holding payment data is more dangerous than a CVSS 9 on a dev laptop that’s never connected to production.
- Is it internet-facing? Exposure to the public internet changes the math completely. Attackers can reach it without ever getting inside your network first.
CVSS gives you a starting point. It’s not a decision-making framework on its own.
A Simple Four-Factor Model for What to Fix First
You don’t need a complex scoring algorithm. You need four questions, asked in order.
1. Is it actively exploited? Check CISA KEV and your threat intelligence feeds. Actively exploited vulnerabilities regardless of score move to the top. No debate needed.
2. Is the affected asset critical to the business? Tag your assets by business impact. A payment processing server, a customer database, an identity provider these aren’t the same as a staging environment. Critical assets get faster SLAs.
3. Is it internet-facing or reachable from an untrusted network? Exposure is a force multiplier. A reachable vulnerability that’s only a CVSS 6 can be more dangerous than an isolated CVSS 9.5 that requires physical access to exploit.
4. What’s the blast radius if it’s exploited? How far can an attacker move from this asset? Systems with connections to your crown jewels customer data, financial systems, identity infrastructure carry more risk than isolated endpoints.
Run your backlog through these four filters. Items that score high across all four get fixed first. Items that score low across all four can wait or be accepted as low risk and documented.
This is the core of attack surface management done right: fewer decisions based on feelings, more decisions based on real exposure.
How to Stop the Backlog From Growing Back
Cutting through your current backlog is only useful if you stop the next one from forming. The teams that keep backlogs under control do three things consistently.
They scan continuously, not quarterly. Vulnerabilities show up between scans. A once-a-quarter snapshot misses everything that appeared in the last 89 days.
They tie remediation to asset owners not just the security team. When a vulnerability lands in a ticket with no owner, it sits. When it lands with the name of the engineer who manages that system and a deadline tied to a compliance SLA, it moves.
They treat the backlog as a risk register, not a to-do list. NIST’s vulnerability management guidance is clear: not every vulnerability needs to be patched. Some can be mitigated with compensating controls. Some can be accepted with documented justification. The goal isn’t a zero-item list it’s a list where every open item has a clear owner, a clear status, and a clear decision behind it.
That shift from “fix everything” to “make a clear decision about everything” is what separates teams that manage risk from teams that just manage panic.
FAQs
What’s the difference between risk-based vulnerability management and just patching by CVSS score?
CVSS scores measure technical severity. Risk-based vulnerability management adds business context asset criticality, exploitability, exposure level, and impact to figure out which vulnerabilities actually need to be fixed first. CVSS is an input, not the full picture.
How do I convince my team to deprioritize a high CVSS vulnerability?
Show context. If the system is isolated, not internet-facing, and the vulnerability isn’t on the CISA KEV list, document the reasoning and move on. The goal is reducing real risk, not achieving a perfect audit score.
How often should we re-run prioritization?
At minimum, whenever a new scan runs or when CISA adds new entries to the KEV catalog. Threat context changes a vulnerability that was low priority last month might be actively exploited today.
What’s the fastest way to start reducing a backlog that’s already out of control?
Start with two filters: KEV-listed vulnerabilities and internet-facing assets. Fix everything that hits both criteria first. That alone will reduce your real exposure faster than working through the list by CVSS score.

Similar Posts
Is the BRICS Cryptocurrency the Game-Changer for the Global Economy?
Sigmacare Review – A Healthcare Solution
What Should You Know Before Starting Cryptocurrency Paper Trading?